LDAP failing
I have 7 domains setup to use the ticket system mainly. I am having issues with one domain recently. All are setup the exact same in the Kace system that I can tell. The scheduled imports used to work and suddenly they are not. Below is the error I received when running the LDAP test. When I do an "LDAP browse" everything works and shows my new users. (Domain name changed to protect the innocent)
Testing LDAP Label Settings...
Testing "Domain" connection to: domain-dc2.domain.local on Port: 389
OK: Connection Successful.
OK: Setting Protocol Version 3 Successful.
OK: Setting LDAP REFERRALS Option 0 Successful.
OK: Search Bind using LDAP supplied credentials Successful.
Applying search filter [(samaccountname=*)]
Error: LDAP search (with filter [(samaccountname=*)]) Failed.
Error: LDAP Test Failed. Closing connection.
Testing "Domain" connection to: domain-dc2.domain.local on Port: 389
OK: Connection Successful.
OK: Setting Protocol Version 3 Successful.
OK: Setting LDAP REFERRALS Option 0 Successful.
OK: Search Bind using LDAP supplied credentials Successful.
Applying search filter [(samaccountname=*)]
Error: LDAP search (with filter [(samaccountname=*)]) Failed.
Error: LDAP Test Failed. Closing connection.
This is the current setting for all domains.
2 Comments
[ + ] Show comments
-
do you have another way of looking at your AD? If it's only one domain that is having the problem maybe it is configured differently than the others? Are you using any LDAP labels or just user imports? - JasonEgg 7 years ago
-
just user imports. I am using the domain administrator account since everyone thinks its a user rights issue. I can use AD explorer with no issues on this domain with that account. any help is appreciated. - looneyk 7 years ago
Answers (3)
Please log in to answer
Posted by:
nshah
7 years ago
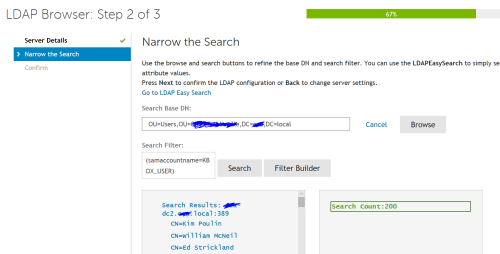
When you do the samaccount name you have to use the KACE variable.
(sAMAccountName=KBOX_USER)
Comments:
-
I added the pic above to show that is the variable that I am using in all domains working and nonworking. - looneyk 7 years ago
Posted by:
anonymous_9363
7 years ago
Run 'AD Explorer' against the domain in question using the 'KBOX_USER' account. That, at least, will tell you whether that user has rights to the domain.
Comments:
-
I am confused at to how to do that when 'KBOX_USER' is a variable used by the Kace appliance, not an actual user in AD. - looneyk 7 years ago
Posted by:
anonymous_9363
7 years ago
So find out the credentials for that account and use it to look up details for the domain using a different utility. It wouldn't be the first time that someone inadvertently assigned zero rights to a user account, especially if your rights are controlled by membership of AD group(s).
Comments:
-
I just used the same account and credentials that are in Kace to run AD Explorer and could connect and see all of my AD. When I use the Kace "LDAP Browser" using same user name and password that is in Kace currently I get returned results and no errors, see new image above. - looneyk 7 years ago


