Securing your network from Java 7 exploits using the K1000
Background
Multiple vulnerabilities in the Java Runtime Environment (found in Java version 6 and 7) have been exploited in the wild as of August 2012. The attacks that were discovered contained two strings that give a clue to the authors, a Chinese hacking group that was responsible for a 2011 attack on at least 48 chemical and defense companies.
On August 31, 2012 Java released a rare out of band patch (they were not due for a patch until October).
http://securitywatch.pcmag.com/none/302218-oracle-quietly-releases-emergency-java-patch
What’s next? Am I protected?
Below are polices that you can create in the K1000 to fully protect your network from the zero-day exploits. The payload for the exploit is delivered via websites so you can disable Java in the browsers or you can uninstall Java until the patch is ready.
Option 1
Create an uninstall script for Java using the Configuration Policy wizard in the Scripting module. The K1000 scripting module contains preconfigured uninstall scripts for inventoried software.
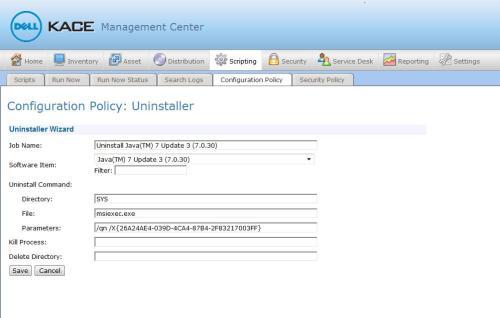
Option 2
Centrally disable Java in the Internet Explorer through the K1000 Scripting module | Security Policy by setting the security to “High” (automatically disables java and ActiveX). For other browsers use the Scripting module | Scripts to create a script or completely disable the other browsers that you do not centrally manage. While the option of blocking Java all together may create some requests from the end users you still have the option to allow certain sites to run java
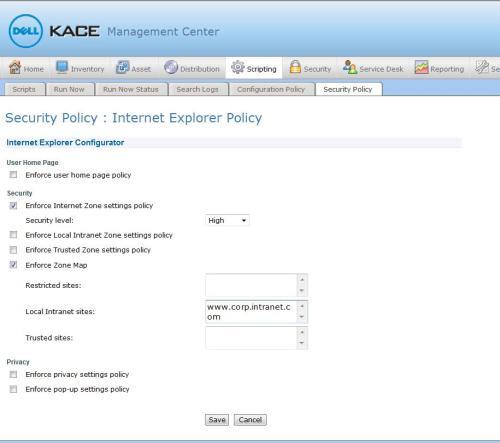
The last step is patching the systems with the latest update from Java and then (optionally) turning Java back on. Going forward you can keep an eye on the earlier versions popping up (if some end user decides to downgrade or does BYOD ) by scheduling a report that looks for versions less than the patched version. If those versions are found you can configure you uninstall script to run on a schedule, removing the threat automatically.


Comments