Why does verifying a file exists when run as the logged in user using %localappdata% still run as the system and not the user?
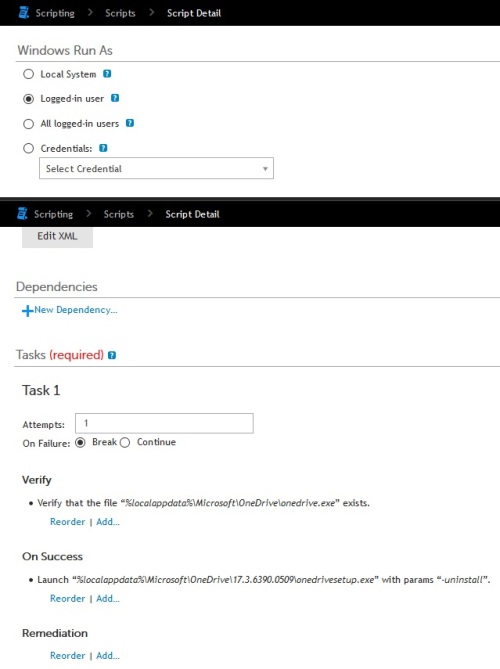
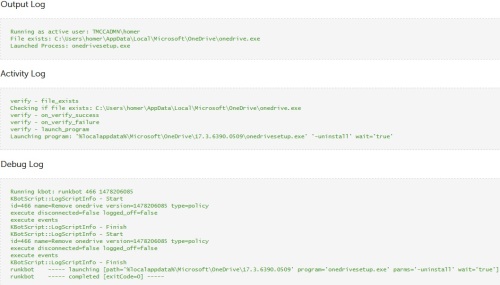
I am trying to create a script in Kace K1000 to check if OneDrive for Business is installed on a computer. In order to do this, I would like to check that the file exists, however the file is located in the local users appdata. When I run the script as the logged in user, and search for %localappdata%\Microsoft\OneDrive\OneDrive.exe it searches here instead C:\windows\system32\config\systemprofile\AppData\Local\Microsoft\OneDrive\OneDrive.exe which means it's running as the system still. Is this a bug in Kace? Or is there a better way to search the local appdata of a user? Any help would be appreciated.
0 Comments
[ + ] Show comments
Answers (2)
Answer Summary:
Please log in to answer
Posted by:
SMal.tmcc
7 years ago
What version is your kbox? Yes there is a bug with some versions
http://www.itninja.com/question/k1000-scripting-verifying-file-exists-as-logged-in-user-in-users-profile
Good news, it is fixed in Version 7 so sit tight for that release.
http://www.itninja.com/question/k1000-scripting-verifying-file-exists-as-logged-in-user-in-users-profile
Good news, it is fixed in Version 7 so sit tight for that release.


Comments:
-
This is exactly what I was hoping for, thanks for the response! - MWettengel 7 years ago
Posted by:
anonymous_9363
7 years ago
Top Answer
Surely there'll be a registry entry in HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall\[ProductCode] | [ProductName]? WSouldn't that be a simpler thing to search for?
Comments:
-
That is actually what I ended up doing, thanks! - MWettengel 7 years ago


