Mozilla Firefox
- 51.x (2 tips)
- 38.x (1 tips)
- 37.x (1 tips)
- 36.x (0 tips)
- 35.x (0 tips)
- 34.x (0 tips)
- 33.x (0 tips)
- 32.x (0 tips)
- 31.x (0 tips)
- 30.x (0 tips)
- 29.x (2 tips)
- 28.x (1 tips)
- 27.x (3 tips)
- 26.x (1 tips)
- 25.x (2 tips)
- 24.0.x (5 tips)
- 24.x (0 tips)
- 23.x (0 tips)
- 22.x (1 tips)
- 21.x (1 tips)
- 20.x (1 tips)
- 19.x (3 tips)
- 18.x (3 tips)
- 17 (Extended Service Release).x (2 tips)
- 16.x (0 tips)
- 15.x (2 tips)
- 14.x (2 tips)
- 13.x (0 tips)
- 11.x (10 tips)
- 10.x (6 tips)
- 9.x (4 tips)
- 8.x (1 tips)
- 7.x (3 tips)
- 6.x (0 tips)
- 5.x (6 tips)
- 4.x (15 tips)
- 3.x (39 tips)
- 2.x (23 tips)
- 1.x (9 tips)
- 0.x (0 tips)
Deployment Tip Summary
Always make sure to use the full setup instead of the online installer (stub).
Before deploying Firefox, unpack the "Firefox Setup 24.0.exe". You will get a setup.exe to install Firefox, and a "core"-Folder, which contains everything that will be in the Installation Directory after installing Firefox.
You can make Settings in the many files inside the core-Folder
Command Line Parameters for Firefox:
-ms Silent Installation
/INI=<full path to configuration ini file> Make settings in setup.ini-File
INSTALLDIR\uninstall\helper.exe /S Silent Uninstallation
Command Line Parameters for Mozilla Firefox Certutil.exe (found in NSS-Tools). This is used to manage Certificates in Firefox via Commandline, because Firefox doesn't use Windows Certutil.exe
-A Add a certificate to the database (create if needed)
All options under -E apply
-B Run a series of certutil commands from a batch file
-i batch-file Specify the batch file
-E Add an Email certificate to the database (create if needed)
-n cert-name Specify the nickname of the certificate to add
-t trustargs Set the certificate trust attributes:
trustargs is of the form x,y,z where x is for SSL, y is for S/MIME,
and z is for code signing. Use ,, for no explicit trust.
p prohibited (explicitly distrusted)
P trusted peer
c valid CA
T trusted CA to issue client certs (implies c)
C trusted CA to issue server certs (implies c)
u user cert
w send warning
g make step-up cert
-f pwfile Specify the password file
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-a The input certificate is encoded in ASCII (RFC1113)
-i input Specify the certificate file (default is stdin)
-C Create a new binary certificate from a BINARY cert request
-c issuer-name The nickname of the issuer cert
-i cert-request The BINARY certificate request file
-o output-cert Output binary cert to this file (default is stdout)
-x Self sign
-m serial-number Cert serial number
-w warp-months Time Warp
-v months-valid Months valid (default is 3)
-f pwfile Specify the password file
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-1 | --keyUsage keyword,keyword,...
Create key usage extension. Possible keywords:
"digitalSignature", "nonRepudiation", "keyEncipherment",
"dataEncipherment", "keyAgreement", "certSigning",
"crlSigning", "critical"
-2 Create basic constraint extension
-3 Create authority key ID extension
-4 Create crl distribution point extension
-5 | --nsCertType keyword,keyword,...
Create netscape cert type extension. Possible keywords:
"sslClient", "sslServer", "smime", "objectSigning",
"sslCA", "smimeCA", "objectSigningCA", "critical".
-6 | --extKeyUsage keyword,keyword,...
Create extended key usage extension. Possible keywords:
"serverAuth", "clientAuth","codeSigning",
"emailProtection", "timeStamp","ocspResponder",
"stepUp", "msTrustListSign", "critical"
-7 emailAddrs Create an email subject alt name extension
-8 dnsNames Create an dns subject alt name extension
-a The input certificate request is encoded in ASCII (RFC1113)
-G Generate a new key pair
-h token-name Name of token in which to generate key (default is internal)
-k key-type Type of key pair to generate ("dsa", "rsa" (default))
-g key-size Key size in bits, (min 512, max 8192, default 1024)
-y exp Set the public exponent value (3, 17, 65537) (rsa only)
-f password-file Specify the password file
-z noisefile Specify the noise file to be used
-q pqgfile read PQG value from pqgfile (dsa only)
-d keydir Key database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-D Delete a certificate from the database
-n cert-name The nickname of the cert to delete
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-U List all modules
-d moddir Module database directory (default is '~/.netscape')
-P dbprefix Cert & Key database prefix
-X force the database to open R/W
-K List all private keys
-h token-name Name of token to search ("all" for all tokens)
-k key-type Key type ("all" (default), "dsa", "rsa")
-n name The nickname of the key or associated certificate
-f password-file Specify the password file
-d keydir Key database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-X force the database to open R/W
-L List all certs, or print out a single named cert
-n cert-name Pretty print named cert (list all if unspecified)
--email email-address
Pretty print cert with email address (list all if unspecified)
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-X force the database to open R/W
-r For single cert, print binary DER encoding
-a For single cert, print ASCII encoding (RFC1113)
-M Modify trust attributes of certificate
-n cert-name The nickname of the cert to modify
-t trustargs Set the certificate trust attributes (see -A above)
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-N Create a new certificate database
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-T Reset the Key database or token
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-h token-name Token to reset (default is internal)
-0 SSO-password Set token's Site Security Officer password
-O Print the chain of a certificate
-n cert-name The nickname of the cert to modify
-d certdir Cert database directory (default is ~/.netscape)
-a Input the certificate in ASCII (RFC1113); default is binary
-P dbprefix Cert & Key database prefix
-X force the database to open R/W
-R Generate a certificate request (stdout)
-s subject Specify the subject name (using RFC1485)
-o output-req Output the cert request to this file
-k key-type-or-id Type of key pair to generate ("dsa", "rsa" (default))
or nickname of the cert key to use
-h token-name Name of token in which to generate key (default is internal)
-g key-size Key size in bits, RSA keys only (min 512, max 8192, default 1024)
-q pqgfile Name of file containing PQG parameters (dsa only)
-f pwfile Specify the password file
-d keydir Key database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-p phone Specify the contact phone number ("123-456-7890")
-a Output the cert request in ASCII (RFC1113); default is binary
See -S for available extension options
-V Validate a certificate
-n cert-name The nickname of the cert to Validate
-b time validity time ("YYMMDDHHMMSS[+HHMM|-HHMM|Z]")
-e Check certificate signature
-u certusage Specify certificate usage:
C SSL Client
V SSL Server
S Email signer
R Email Recipient
O OCSP status responder
J Object signer
-d certdir Cert database directory (default is ~/.netscape)
-a Input the certificate in ASCII (RFC1113); default is binary
-P dbprefix Cert & Key database prefix
-X force the database to open R/W
-W Change the key database password
-d certdir cert and key database directory
-f pwfile Specify a file with the current password
-@ newpwfile Specify a file with the new password in two lines
--upgrade-merge Upgrade an old database and merge it into a new one
-d certdir Cert database directory to merge into (default is ~/.netscape)
-P dbprefix Cert & Key database prefix of the target database
-f pwfile Specify the password file for the target database
--source-dir certdir
Cert database directory to upgrade from
--soruce-prefix dbprefix
Cert & Key database prefix of the upgrade database
--upgrade-id uniqueID
Unique identifier for the upgrade database
--upgrade-token-name name
Name of the token while it is in upgrade state
-@ pwfile Specify the password file for the upgrade database
--merge Merge source database into the target database
-d certdir Cert database directory of target (default is ~/.netscape)
-P dbprefix Cert & Key database prefix of the target database
-f pwfile Specify the password file for the target database
--source-dir certdir
Cert database directory of the source database
--source-prefix dbprefix
Cert & Key database prefix of the source database
-@ pwfile Specify the password file for the source database
-S Make a certificate and add to database
-n key-name Specify the nickname of the cert
-s subject Specify the subject name (using RFC1485)
-c issuer-name The nickname of the issuer cert
-t trustargs Set the certificate trust attributes (see -A above)
-k key-type-or-id Type of key pair to generate ("dsa", "rsa" (default))
-h token-name Name of token in which to generate key (default is internal)
-g key-size Key size in bits, RSA keys only (min 512, max 8192, default
1024)
-q pqgfile Name of file containing PQG parameters (dsa only)
-x Self sign
-m serial-number Cert serial number
-w warp-months Time Warp
-v months-valid Months valid (default is 3)
-f pwfile Specify the password file
-d certdir Cert database directory (default is ~/.netscape)
-P dbprefix Cert & Key database prefix
-p phone Specify the contact phone number ("123-456-7890")
-1 Create key usage extension
-2 Create basic constraint extension
-3 Create authority key ID extension
-4 Create crl distribution point extension
-5 Create netscape cert type extension
-6 Create extended key usage extension
-7 emailAddrs Create an email subject alt name extension
-8 DNS-names Create a DNS subject alt name extension
--extAIA Create an Authority Information Access extension
--extSIA Create a Subject Information Access extension
--extCP Create a Certificate Policies extension
--extPM Create a Policy Mappings extension
--extPC Create a Policy Constraints extension
--extIA Create an Inhibit Any Policy extension
--extSKID Create a subject key ID extension
-
I have a compiled certutil of Firefox which i downloaded from a third party site. And tried to push it using the command line
certutil.exe -A -a -n "nickname of the certificate" -t "U,U,U" -d "location of the certificate". That was a bummer to me. If u made the command line work please do let me know. - Sidhugadu 10 years ago
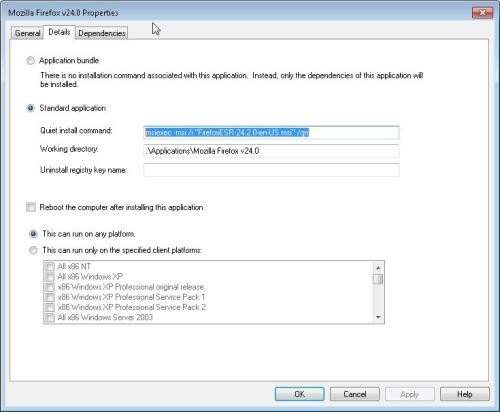
Using a MSI file I use this:
msiexec -msi /i "FirefoxESR-24.2.0-en-US.msi" /qn
I downloaded mine from http://www.frontmotion.com/Firefox/download_firefox.htm
I use it on my MDT 2012 server
Installing addins or extensions
.\firefox.exe" -ProfileManager -install-global-extension "<path-to-extension>\extname.xpi"
http://kb.mozillazine.org/Command_line_arguments
Install addon as above, then copy the extracted add on from the current user Mozilla profile
Then put the extracted files somewhere you can run the cmd from
Use MSI by FrontMotion ? http://www.frontmotion.com/Firefox/download_firefox.htm
Msiexec /i Firefox.MSI TRANSFORMS=Firefox.mst /qn /norestart
In my company, i use a personnal script .bat with SCCM 2012 :
@ECHO On & @SET programfiles32=%ProgramFiles%& @IF NOT "%ProgramFiles(x86)%"=="" @SET programfiles32=%ProgramFiles(x86)%& @SETLOCAL ENABLEEXTENSIONS & @CD /D "%~dp0"
REM Fermer Firefox
:killfirefox
taskkill /f /t /im firefox.exe
tasklist /FI "IMAGENAME eq firefox.exe" 2>NUL | find /I /N "firefox.exe">NUL
if "%ERRORLEVEL%"=="0" GOTO killfirefox
REM Desinstaller l'ancienne version (21.0) - MSI
msiexec /x {D3947DE2-A23C-457B-85FC-512390244993} /q /norestart
REM Desinstaller l'ancienne version (3.6 -> 21.0) - EXE
if exist "%programfiles32%\Mozilla Firefox\uninstall" (
"%programfiles32%\Mozilla Firefox\uninstall\helper.exe" /S
ping 127.0.0.1 -n 10 > NUL
)
REM Installer la nouvelle version (25.0) - MSI
msiexec /i "%~dp0Firefox-24.0-fr.msi" TRANSFORMS="%~dp0Firefox_24.0_GHdC.mst" /qn /norestart
copy /Y "%~dp0override.ini" "%programfiles32%\Mozilla Firefox\"
copy /Y "%~dp0firefox.cfg" "%programfiles32%\Mozilla Firefox\"
copy /Y "%~dp0local-settings.js" "%programfiles32%\Mozilla Firefox\defaults\pref"
exit
Inventory Records (0)
View inventory records anonymously contributed by opt-in users of the K1000 Systems Management Appliance.
