What is the best way to track, prevent, and uninstall rogue software?
What is the best way to track, prevent, and uninstall rogue software? Process or steps?
K1000 version 5.4xx
Thanks
Answers (3)
For tracking: I setup an automated report that displayed all software installed in the last 24 hours and reviewed that report each morning. Being proactive is one of the best ways to mitigate malware.
Prevention: Don't have your users running as local admins. Have a strong antivirus installed on all of your systems. Don't allow USB drives to freely connect to your systems with something like Sophos or GPO.
Uninstall: See your other two questions on the same topic. I setup a Managed Installation associated with a Smart Label on the K1000 that would detect rogue software and automatically uninstall it using the command line. For more malicious malware, check out my blog post on using Sysinternals tools for malware remediation: http://www.itninja.com/blog/view/malware-hunting-with-sysinternals-tools
Comments:
-
Could you post the SQL for that report please? The software installed in the last 24 hours report. - AFCUjstrick 10 years ago
-
Edit: Found it. Thanks! - AFCUjstrick 10 years ago
-
I know you said you found it, but just in case anyone else needs it this is a variation I use.
SELECT DISTINCT NAME, VALUE1 AS 'Software Display Name', VALUE2 AS 'Software Version'
FROM ASSET_HISTORY A
WHERE CHANGE_TYPE = 'DETECTED'
AND FIELD_NAME = 'SOFTWARE'
AND TIME > DATE_SUB(NOW(), INTERVAL 1 DAY)
ORDER BY NAME, VALUE1 - dugullett 10 years ago
-
Nice, thank you. I will test it out. - ITROCKS 10 years ago
-
Thanks dugullett. - ITROCKS 10 years ago
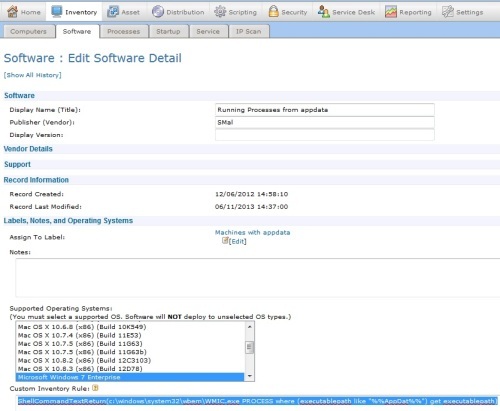
I created a custom software inventory that watches for process's running from the user app data area. 90-95% it will be malwares home. this is the fixed code
Comments:
-
try this new line
ShellCommandTextReturn(c:\windows\system32\wbem\WMIC.exe PROCESS where (executablepath like "%%AppDat%%") get executablepath)
much cleaner - SMal.tmcc 10 years ago-
I'd be curious what you do with this information? I setup the custom inventory like you showed above, but all the applications it shows are legit for my system.
Do you have a report setup to notify you? - AFCUjstrick 10 years ago-
I look at the list and if anything is not IT approved I create a work order to investigate and remove or create a MI uninstall to kill it.
If it is IT approved or gets IT approved we then let that one go. - SMal.tmcc 10 years ago -
posted new line above, see picture above for cleaner out put - SMal.tmcc 10 years ago
-
Awesome! Thank you! - ITROCKS 10 years ago
-
Just a note on this report.
We have found that when a new user signs on to an existing device, creating a new profile, softwares that run any type of install routine in the new profile (Google Chrome as an example), show up in the report. This could lead to a false-positive type of problem in environments that are tightly managed.
Other than the above issue it is a very helpful report. I am working on adding the logged in user to it as time permits. Will post the results when I get it working.
John - jmarotto 10 years ago




