Want to see which users/groups have local admin rights on your machines? Create these Custom Inventory Rules to list that in the inventory record!
PC Rule
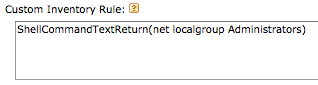
For PCs, create a custom inventory rule (Inventory -> Software -> Create New) and fill the CIR box with the following command:
ShellCommandTextReturn(net localgroup Administrators)
I would suggest naming the rule "Local Administrators" for simplicity.
Make sure to select all Windows versions and your machines should start checking in with results like this:
1) Local Administrators:Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
AD\jsmith
AD\Domain Admins
AD\DEPT-ADM
Administrator
LOCAL-ADMIN
The command completed successfully.
[string]
OS X Rule
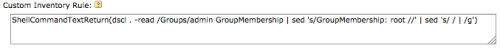
For Macs, create another custom inventory rule (Inventory -> Software -> Create New) and fill the CIR box with the following command:
Update: Based on a tip from serkowski, I have changed the use of awk to sed, as seen below.
ShellCommandTextReturn(dscl . -read /Groups/admin GroupMembership | sed 's/GroupMembership: root //' | sed 's/ / | /g')
Piping the results of the dscl query to two consecutive sed (stream editor) commands will remove the "GroupMembership:" prefix, and will exclude the root account, and will then add pipes(|) between resulting accounts.
I named this rule OS X Local Administrators, again for simplicity.
Make sure all versions of OS X are selected, and your macs should start checking in with results like this:
1) OS X Local Administrators: local-admin | jsmith [string]
Reporting
From this point, you can create reports to detect common accounts, or even to detect if the current logged in user is an admin. Here is an example of detecting if the current logged in user is an admin. Replace the ##### examples with the software IDs of the Custom Inventory Rules you created above:
SELECT * FROM MACHINE
JOIN MACHINE_CUSTOM_INVENTORY ON MACHINE_CUSTOM_INVENTORY.ID=MACHINE.ID AND (SOFTWARE_ID=##### OR SOFTWARE_ID=#####)
WHERE MACHINE_CUSTOM_INVENTORY.STR_FIELD_VALUE LIKE CONCAT('%', MACHINE.USER, '%') AND MACHINE.USER !=''

Any ideas? Thanks. - AFCUjstrick 12 years ago
So how do I prevent the command from running on the wrong OS and producing a screenful of usage information?
Or worse, the command is successful and causes an unintended result? - serkowski 12 years ago
A better rule for OSX is:
ShellCommandTextReturn(dscl . -read /Groups/admin GroupMembership | sed 's/GroupMembership: root //')
And a rule for Linux looks like:
ShellCommandTextReturn(grep wheel /etc/group | sed 's/^.*:root,//') - serkowski 12 years ago
net localgroup Administrators | FINDSTR /V "ADMIN1" | FINDSTR /V "ADMIN2" - jaredv 11 years ago
ShellCommandTextReturn(net localgroup Administrators | FINDSTR /V "Administrator" | FINDSTR /V "Members" | FINDSTR /V "The command completed successfully." | FINDSTR /V "DOMAIN\Domain Admins")
The command runs fine in a prompt and has a clean output. - mmcspadd 11 years ago
[Fri Jun 14 14:46:46 2013] The option /V is unknown.
[Fri Jun 14 14:46:46 2013] The syntax of this command is:
[Fri Jun 14 14:46:46 2013] NET LOCALGROUP
[groupname [/COMMENT:"text"]] [/DOMAIN]
groupname {/ADD [/COMMENT:"text"] | /DELETE} [/DOMAIN]
groupname name [...] {/ADD | /DELETE} [/DOMAIN]
[Fri Jun 14 14:46:46 2013] More help is available by typing NET HELPMSG 3506.
It's as though the K1000 is trying to use the /V argument against the net command, rather than findstr. Any suggestions? - brupnick 10 years ago
net localgroup "Power Users" - jaredv 11 years ago
ShellCommandTextReturn(cmd /c net localgroup Administrators) - StockTrader 10 years ago
select SOFTWARE.DISPLAY_NAME,MACHINE_CUSTOM_INVENTORY.SOFTWARE_ID
from SOFTWARE,MACHINE_CUSTOM_INVENTORY
where
SOFTWARE.ID=MACHINE_CUSTOM_INVENTORY.SOFTWARE_ID
This will give you all the IDs of the custom field you created. - StockTrader 10 years ago
That's my query:
----
select SOFTWARE_ID,DISPLAY_NAME, STR_FIELD_VALUE , USER ,MACHINE.NAME FROM
(select SOFTWARE.DISPLAY_NAME,MACHINE_CUSTOM_INVENTORY.SOFTWARE_ID,MACHINE_CUSTOM_INVENTORY.ID,MACHINE_CUSTOM_INVENTORY.STR_FIELD_VALUE
from SOFTWARE,MACHINE_CUSTOM_INVENTORY
where
SOFTWARE.ID=MACHINE_CUSTOM_INVENTORY.SOFTWARE_ID AND
DISPLAY_NAME LIKE '######' ) AS AAA,MACHINE
WHERE
AAA.ID=MACHINE.ID AND
MACHINE.USER !=''AND
AAA.STR_FIELD_VALUE LIKE CONCAT('%', MACHINE.USER, '%')
---
Substitute ##### with the name of field.
Marco - StockTrader - StockTrader 10 years ago
select
MACHINE.NAME, MACHINE.USER, CI.STR_FIELD_VALUE
from
MACHINE
INNER JOIN
MACHINE_CUSTOM_INVENTORY CI ON MACHINE.ID = CI.ID
INNER JOIN
SOFTWARE ON SOFTWARE.ID = CI.SOFTWARE_ID
WHERE
SOFTWARE.DISPLAY_NAME LIKE '######'
AND MACHINE.USER != ''
AND CI.STR_FIELD_VALUE LIKE CONCAT('%', MACHINE.USER, '%')
Feel free to adjust the SELECT statement to your needs :-)
Marco. - StockTrader 10 years ago
http://www.itninja.com/question/is-there-a-way-to-develop-a-report-on-who-has-admin-rights-on-their-pc - SMal.tmcc 10 years ago
ShellCommandTextReturn(cmd.exe /c net localgroup Administrators) - awingren 10 years ago